AWS News Blog
Streamline AMI Maintenance and Patching Using Amazon EC2 Systems Manager | Automation
Here to tell you about using Automation to streamline AMI maintenance and patching is Taylor Anderson, a Senior Product Manager with EC2.
-Ana
Last December at re:Invent, we launched Amazon EC2 Systems Manager, which helps you automatically collect software inventory, apply OS patches, create system images, and configure Windows and Linux operating systems. These capabilities enable automated configuration and ongoing management of systems at scale, and help maintain software compliance for instances running in Amazon EC2 or on-premises.
One feature within Systems Manager is Automation, which can be used to patch, update agents, or bake applications into an Amazon Machine Image (AMI). With Automation, you can avoid the time and effort associated with manual image updates, and instead build AMIs through a streamlined, repeatable, and auditable process.
Recently, we released the first public document for Automation: AWS-UpdateLinuxAmi. This document allows you to automate patching of Ubuntu, CentOS, RHEL, and Amazon Linux AMIs, as well as automating the installation of additional site-specific packages and configurations.
More importantly, it makes it easy to get started with Automation, eliminating the need to first write an Automation document. AWS-UpdateLinuxAmi can also be used as a template when building your own Automation workflow. Windows users can expect the equivalent document―AWS-UpdateWindowsAmi―in the coming weeks.
AWS-UpdateLinuxAmi automates the following workflow:
- Launch a temporary EC2 instance from a source Linux AMI.
- Update the instance.
- Invoke a user-provided, pre-update hook script on the instance (optional).
- Update any AWS tools and agents on the instance, if present.
- Update the instance’s distribution packages using the native package manager.
- Invoke a user-provided post-update hook script on the instance (optional).
- Stop the temporary instance.
- Create a new AMI from the stopped instance.
- Terminate the instance.
Warning: Creation of an AMI from a running instance carries a risk that credentials, secrets, or other confidential information from that instance may be recorded to the new image. Use caution when managing AMIs created by this process.
Configuring roles and permissions for Automation
If you haven’t used Automation before, you need to configure IAM roles and permissions. This includes creating a service role for Automation, assigning a passrole to authorize a user to provide the service role, and creating an instance role to enable instance management under Systems Manager. For more details, see Configuring Access to Automation.
Executing Automation
- In the EC2 console, choose Systems Manager Services, Automations.
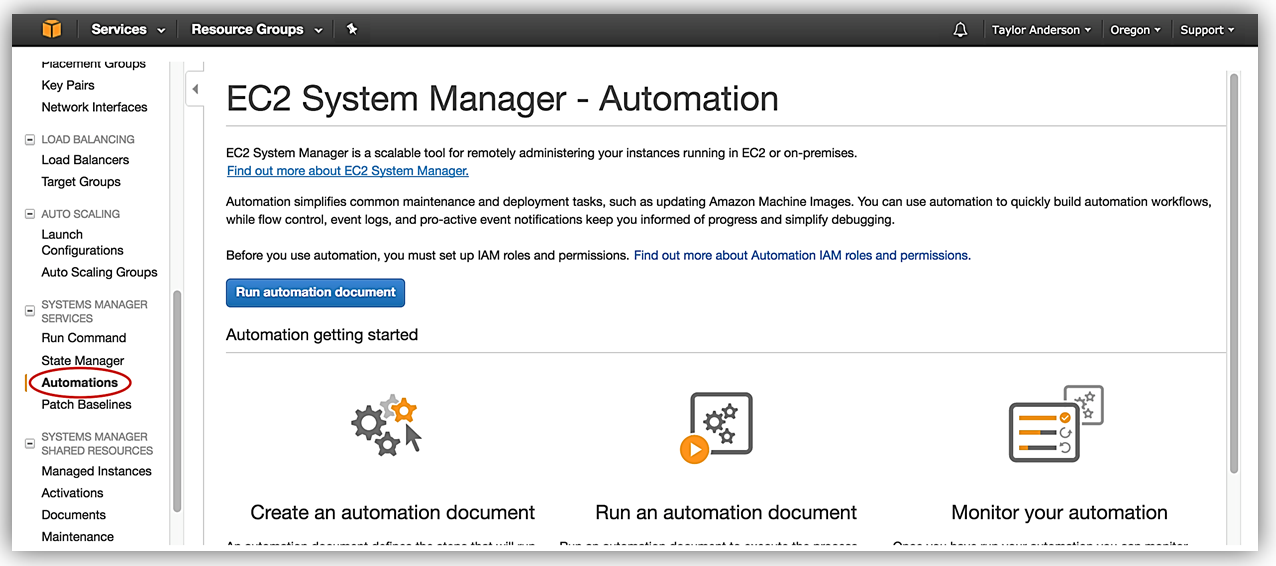
- Choose Run automation document
- Expand Document name and choose AWS-UpdateLinuxAmi.
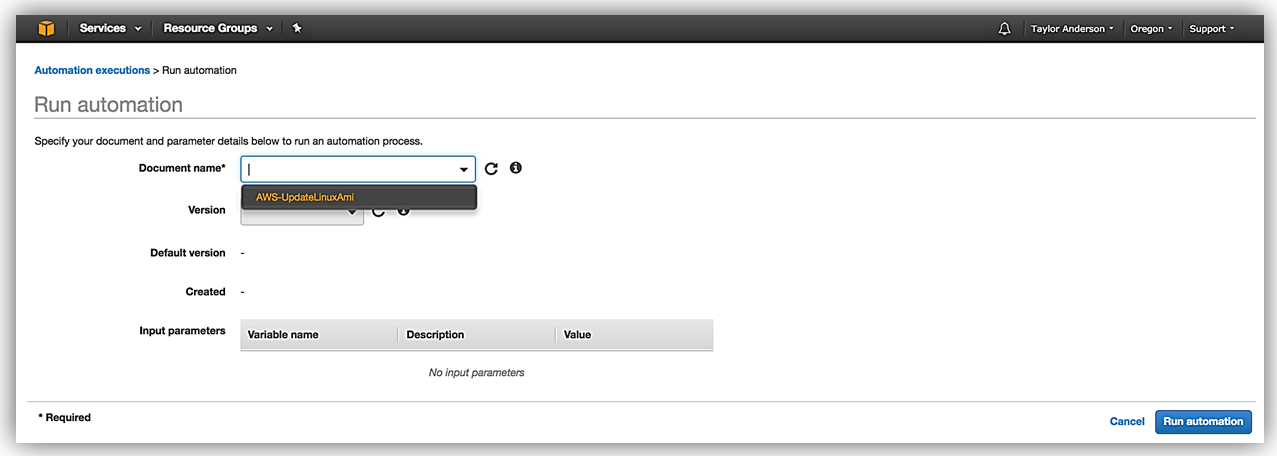
- Choose the latest document version.
- For SourceAmiId, enter the ID of the Linux AMI to update.
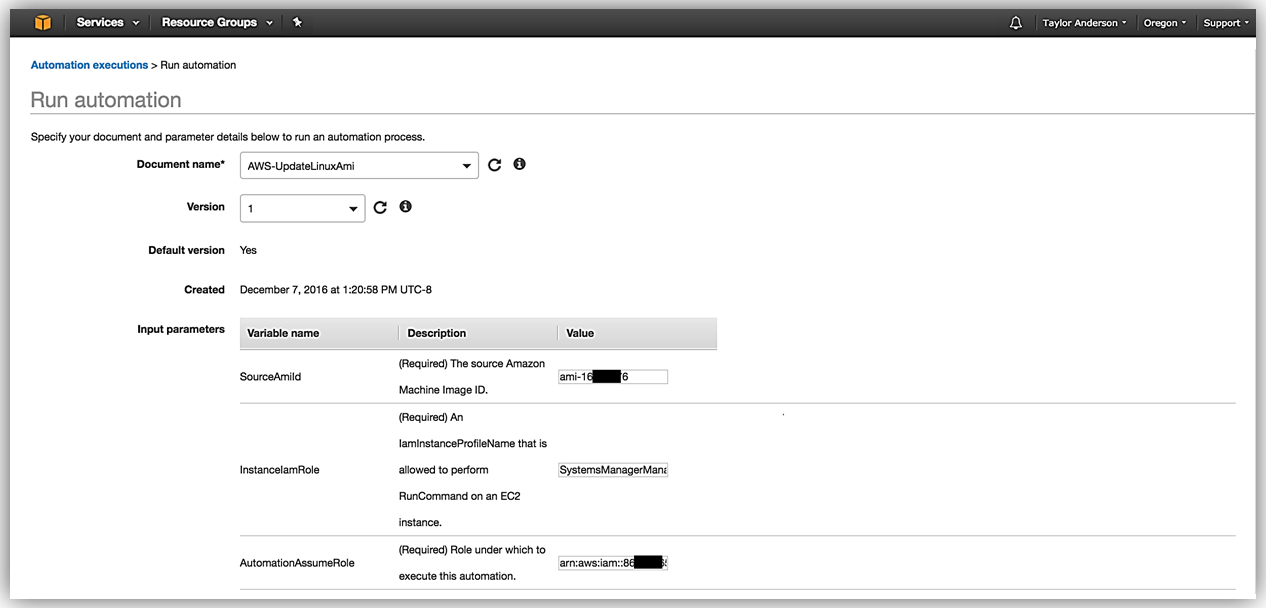
- For InstanceIamRole, enter the name of the instance role you created enabling Systems Manager to manage an instance (that is, it includes the AmazonEC2RoleforSSM managed policy). For more details, see Configuring Access to Automation.
- For AutomationAssumeRole, enter the ARN of the service role you created for Automation. For more details, see Configuring Access to Automation.
- Choose Run Automation.
- Monitor progress in the Automation Steps tab, and view step-level outputs.
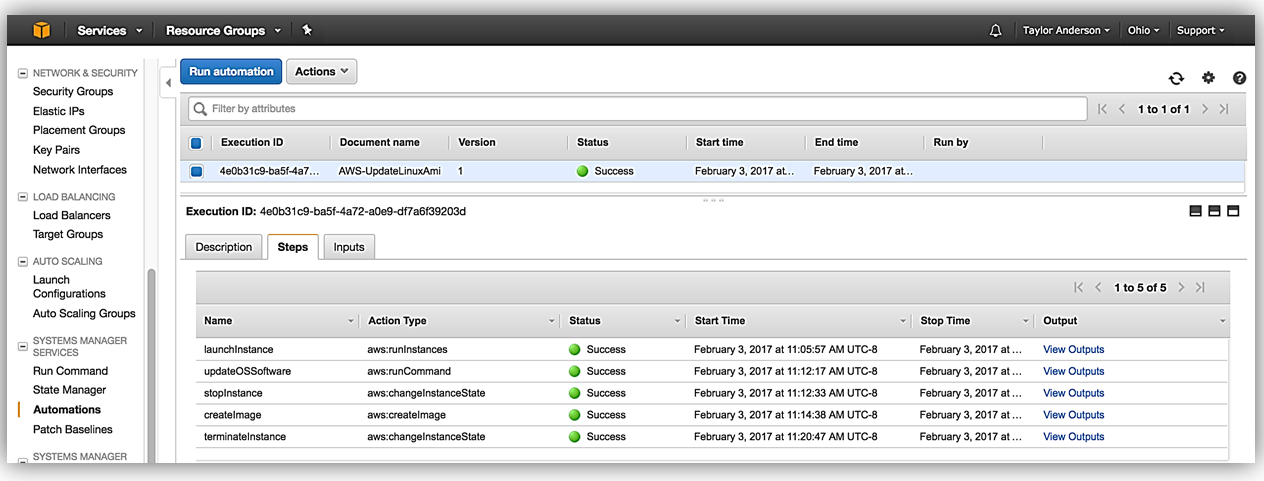
After execution is complete, choose Description to view any outputs returned by the workflow. In this example, AWS-UpdateLinuxAmi returns the new AMI ID.
Next, choose Images, AMIs to view your new AMI.
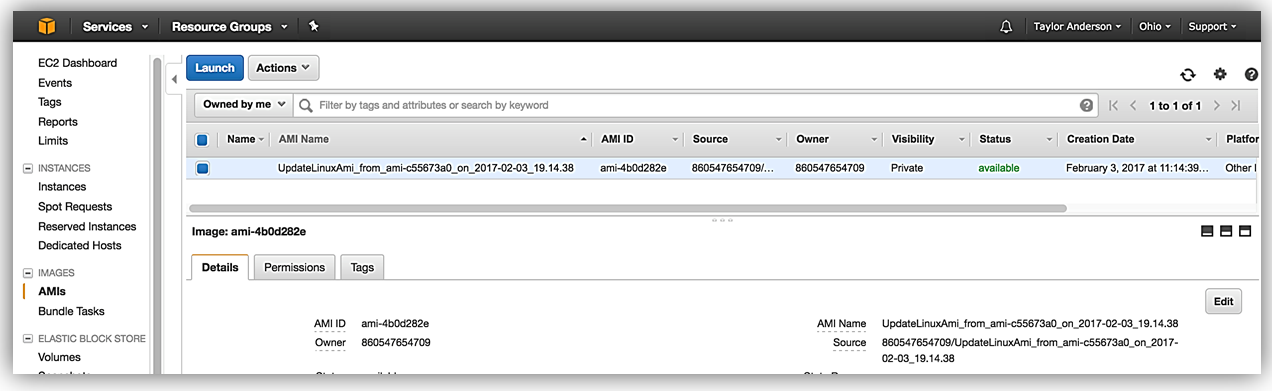
There is no additional charge to use the Automation service, and any resources created by a workflow incur nominal charges. Note that if you terminate AWS-UpdateLinuxAmi before reaching the “Terminate Instance” step, shut down the temporary instance created by the workflow.
A CLI walkthrough of the above steps can be found at Automation CLI Walkthrough: Patch a Linux AMI.
Conclusion
Now that you’ve successfully run AWS-UpdateLinuxAmi, you may want to create default values for the service and instance roles. You can customize your workflow by creating your own Automation document based on AWS-UpdateLinuxAmi. For more details, see Create an Automaton Document. After you’ve created your document, you can write additional steps and add them to the workflow.
Example steps include:
- Updating an Auto Scaling group with the new AMI ID (aws:invokeLambdaFunction action type)
- Creating an encrypted copy of your new AMI (aws:encrypedCopy action type)
- Validating your new AMI using Run Command with the RunPowerShellScript document (aws:runCommand action type)
Automation also makes a great addition to a CI/CD pipeline for application bake-in, and can be invoked as a CLI build step in Jenkins. For details on these examples, be sure to check out the Automation technical documentation. For updates on Automation, Amazon EC2 Systems Manager, Amazon CloudFormation, AWS Config, AWS OpsWorks and other management services, be sure to follow the all-new Management Tools blog.