AWS News Blog
Identity and Access Management in the AWS Management Console
The AWS Management Console now includes support for Identity and Access Management (IAM). You can create and manage users, groups, and policies with a couple of mouse clicks. Read on to learn more about this new feature, or read my other post to learn more about IAM.
There’s a new IAM tab on the AWS Management Console:
This tab lets you create and manage IAM users, groups of IAM users, their permissions, and their security credentials:
You can create a new group of users by clicking on this button on the IAM Dashboard:
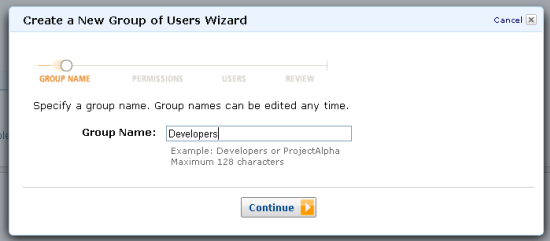
The Create a New Group of Users Wizard will be displayed. The first step is to enter a group name:
You can select a predefined policy template, or you can build your own using the AWS Policy Generator (you can add additional policies to the group after you create it if you’d like). The wizard includes a template for every service that currently works with IAM to make it easy for you to get started.
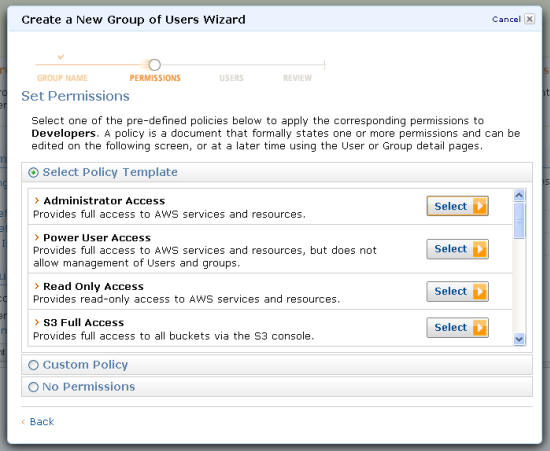
After selecting a policy, you can make any necessary changes to the policy document before you use it to create the group. You could, for example, add restrictions based on IP address or the use of SSL connections:
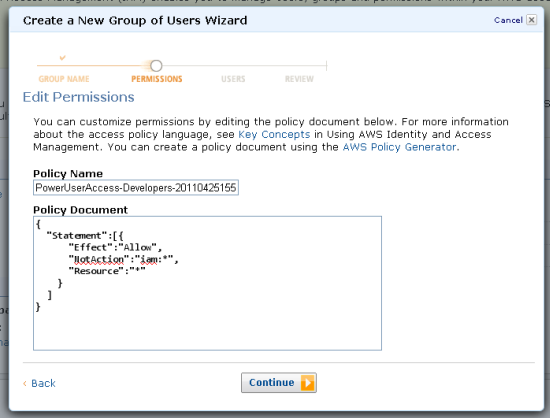
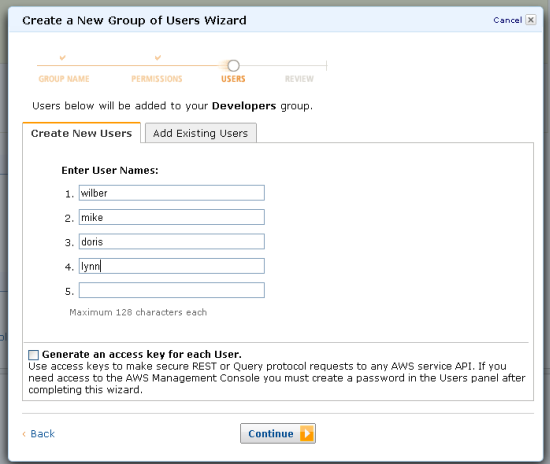
The next step is to create the users for the group (you can also add existing users to it):
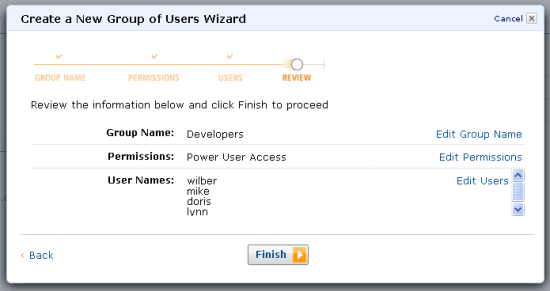
After a final review, you can create the group by clicking on the Finish button:
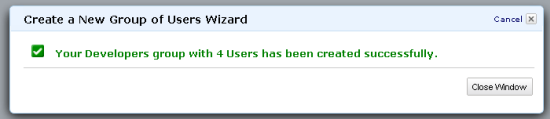
You can also manage security policies, AWS credentials, console sign-in credentials, and Multi-Factor Authentication for any user:
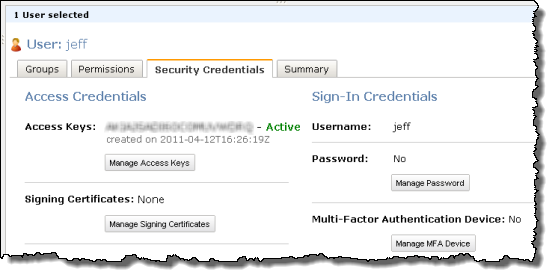
If you set the sign-in credentials for an IAM user, the user can sign in to AWS Management Console using their credentials:
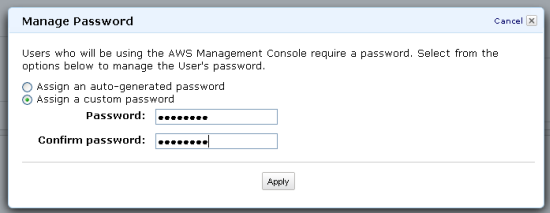
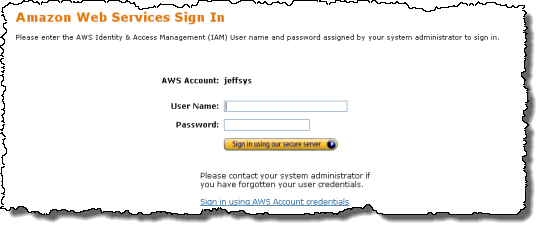
The new IAM console lets you create an account alias. The account alias is used to identify the account on the user-level sign-in page:
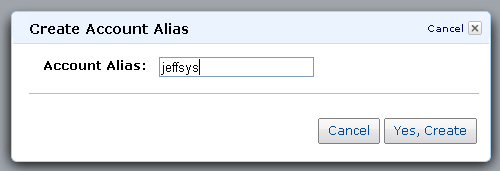
In the example above, I have created the alias “jeffsys” for my AWS account. The user-level sign-in page is at https://jeffsys.signin.thinkwithwp.com/console .
The user’s actions within the console will be regulated by the permissions associated with the user.
— Jeff;