- AWS Solutions Library›
- Guidance for Product Traceability on AWS
Guidance for Product Traceability on AWS
Overview
How it works
Overview
This overview architecture shows a process flow for adding traceability and transparency to a product supply chain.
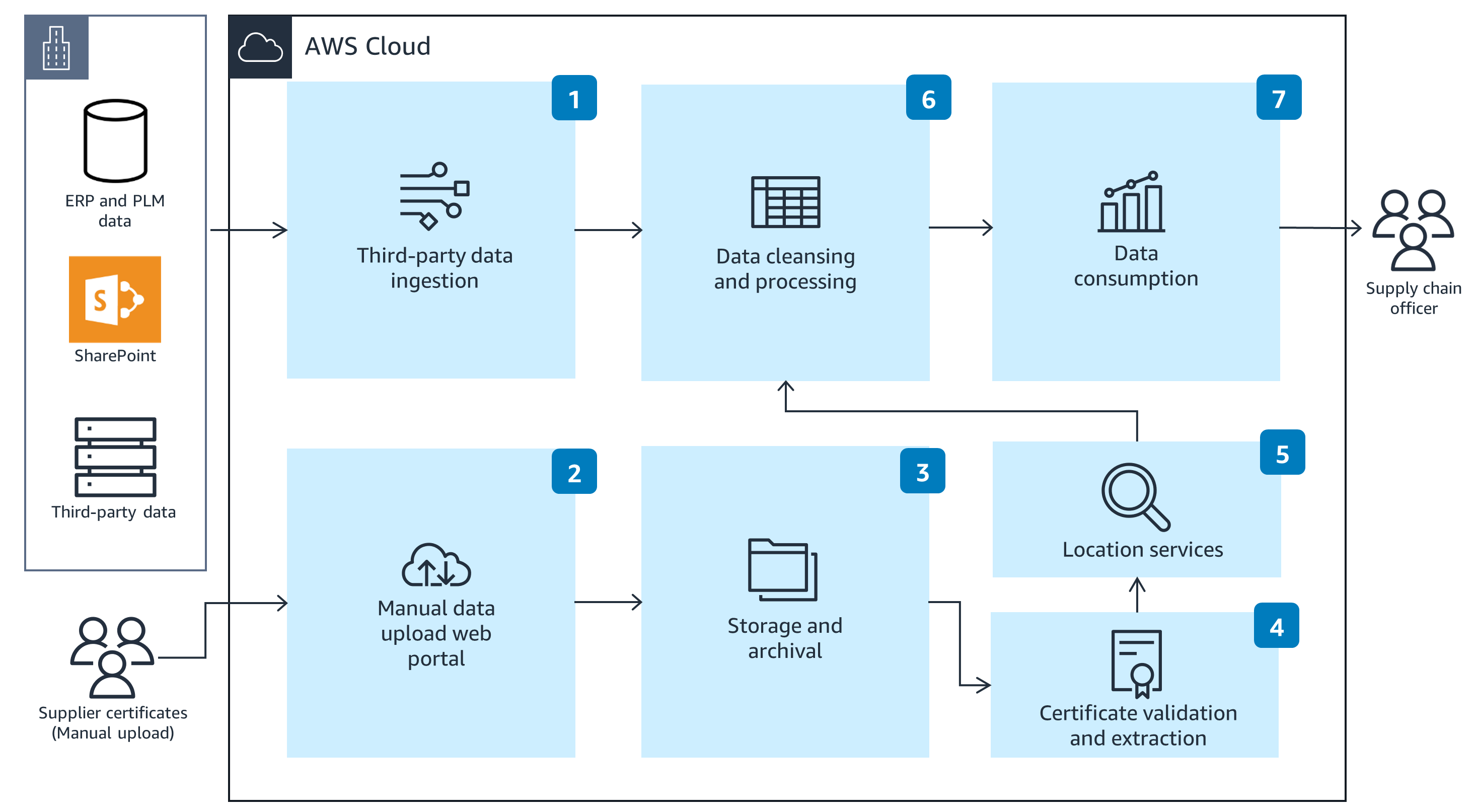
Detailed Architecture
This detailed architecture shows a process flow for adding traceability and transparency to a product supply chain.
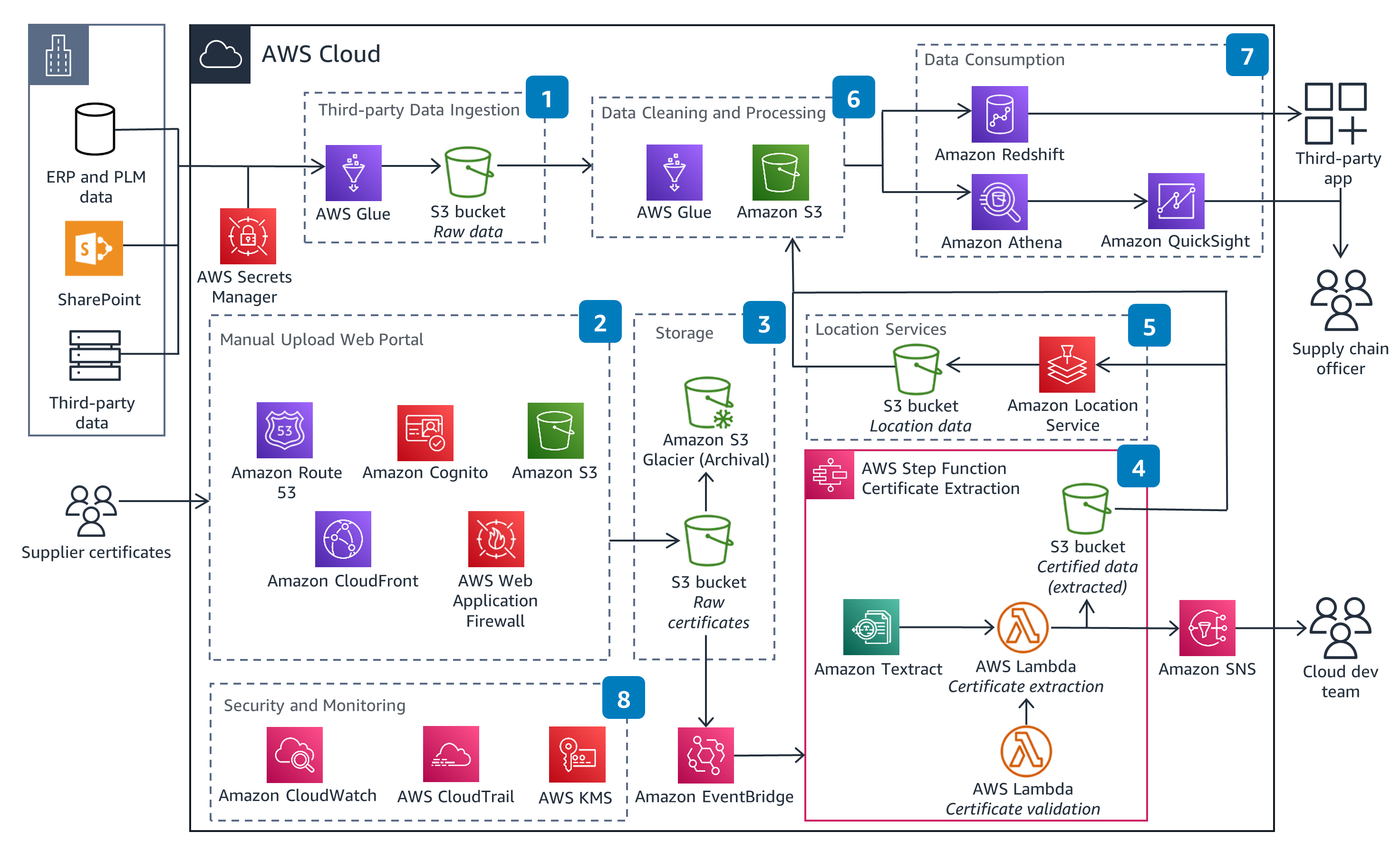
Well-Architected Pillars
The architecture diagram above is an example of a Solution created with Well-Architected best practices in mind. To be fully Well-Architected, you should follow as many Well-Architected best practices as possible.
This Guidance is deployed using AWS Cloud Development Kit (AWS CDK). Changes to the main branch of your repository of choice are propagated to the Guidance infrastructure through AWS CodePipeline.
Read the Operational Excellence whitepaperThis Guidance uses AWS WAF, Amazon Cognito, and AWS Certificate Manager (ACM) to secure access to its hosted upload portal, restricting access to services and protecting them from attacks. All data is encrypted at rest using AWS KMS keys.
The load balancer will ensure the health of the hosted upload portal alongside built-in autoscaling for services. It is critical that the extraction be done within a Step Function that includes a retry mechanism. Otherwise, you may encounter a bottleneck in Amazon Textract due to account-level concurrency limits that can only be increased by contacting AWS support. It is possible for the extraction Lambda function to fail if too many certificates are uploaded at once. As such, the Step Function should include a fail-retry check to address failures that occur as result of Textract throttling.
We selected the services in this Guidance to create a serverless architecture. The Guidance uses automation to minimize infrastructure management and user intervention. The architecture is also decoupled so that different functions can run independently from one another.
All data is stored in Amazon S3, with lifecycle policies that automatically archive old certificates. This allows for cost optimization while still adhering to data retention regulations.
All components of this Guidance are serverless and scale automatically. This approach ensures minimal energy consumption while maintaining high availability.
Read the Sustainability whitepaperImplementation resources
Disclaimer
Did you find what you were looking for today?
Let us know so we can improve the quality of the content on our pages