Category: AWS Management Console
AWS Management Console for iPhone
Back in January we released our first Management Console mobile app for Android users.
Were now pleased to announce the availability of the AWS Console for iPhone! The app summarizes the status of your EC2 instances, CloudWatch alarms, total service charges, and AWS Service Health. You can view all of your EC2 instances, filter and search for a specific instance, view instance details, and stop or reboot an instance. You can also filter and search for CloudWatch alarms and view CloudWatch metrics to monitor the health of your resources. As with the web-based management console, sign-in is as simple as entering your AWS or IAM credentials.
Here’s a tour:
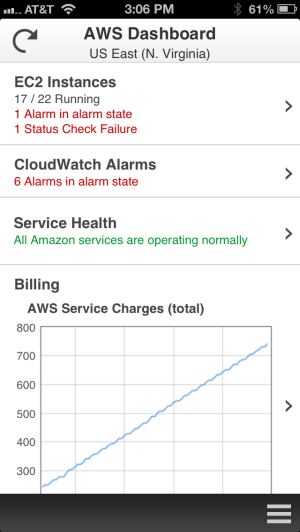
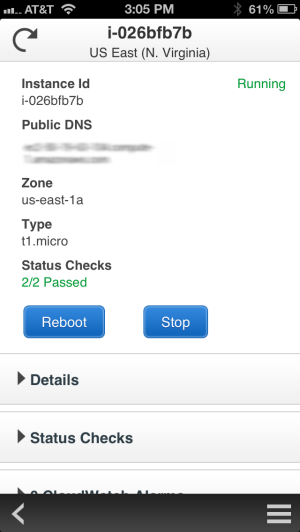
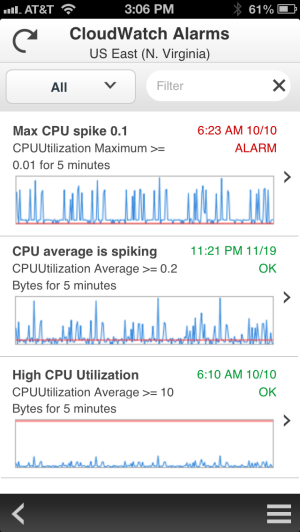
We plan to add support for additional services very quickly, so stay tuned (and use the app’s feedback function to tell us what you think).
You can download the console now and get started right away!
— Jeff;
AWS Management Console Improvements – Tablet and Mobile Support
Managing your AWS resources has become easier and more direct over the years! Let’s do a quick recap before we dig in:
- We launched Amazon SQS (2004) and Amazon S3 (2006) as pure APIs, with no tool support whatsoever. Developers were quick to build all sorts of interesting tools around the web service APIs.
- Later in 2006, we introduced Amazon EC2, this time with a set of command-line tools.
- Sometime in 2007 we entered the visual, browser-based era with the release of ElasticFox.
- In early 2009 we released the AWS Management Console and have focused our development efforts there ever since that launch.
Over the years we’ve made many incremental improvements to the AWS Management Console. We’ve also improved the overall look and feel a couple of times. The goal remains unchanged – to provide you with a clean and efficient way to see and manage your AWS resources.
Today we are ready to take another step forward. We’re making some big improvements to the existing Console, and we’re also introducing a brand-new Console App for Android devices. In this post I’ll give you a visual tour of both applications..
AWS Management Console Improvements
We heard your feedback that the growing number of services in the Management Console (21 and counting), increased service functionality, and new form factors such as tablets, required an update to our designs. Our focus is to make AWS easier to use by increasing customizability and improving information display on your screen of choice.
We started with a focus on customization to make the Console work better for you. We moved Region selection into the Consoles navigation and made it work seamlessly across all of the services. You can also customize the Console navigation with shortcuts to the AWS services that you use the most often:
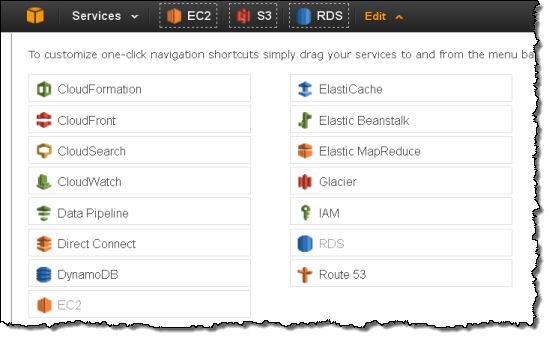
We learned that many Console users spent a lot of time alternately selecting one of a pair of AWS resources in order to compare and contrast certain settings. This wasn’t a good use of your time, so we added inline resource summaries to give you quick access to key resource attributes.
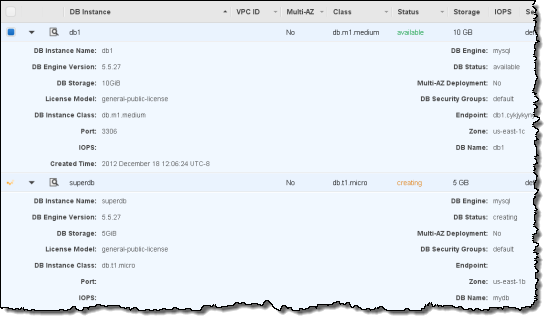
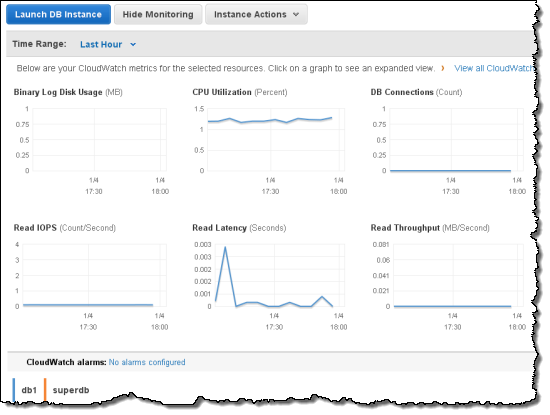
We then reviewed the Console’s information management and display features to improve readability and to put your information front and center. We learned that monitoring resource statistics is one of the most frequent actions and users wanted more space to view graphs. The new Monitoring View makes it easier for you to see statistics for your resources. You can easily filter your resources and hit the new Select All button to see stacked graphs for your resources. You can even change this view to see all the graphs or individual large graphs on one screen.
We also learned that many users wanted as much space as possible for table information. To accommodate this, we added a collapse option to the side navigation pane and moved the table details to let the table fill the screen.
Finally, we know that many of you use (or would like to use) the Console from your tablet device, so we now support endless scrolling within the current page. Your resources are just a swipe away! We also optimized the use of horizontal and vertical space and made the buttons and selectors large enough to ensure easy access.
These improvements will be rolled out across the AWS services on slightly different schedules. We look forward to your feedback on these new designs!
AWS Management Console App
This new app provides mobile-relevant tasks that are a good companion to the full web experience including the ability to quickly and easily view and manage your existing EC2 instances and CloudWatch alarms from your Android phone. You can view your total AWS service charges and switch between AWS accounts and regions from within the app. As with the web-based management console, sign-in is as simple as entering your AWS or IAM credentials.
You can:
- View a summary of your EC2 instances, CloudWatch alarms, total service charges, and the AWS Service Health status, with optional filtering on the instances and alarms.
- Look at EC2 instance metrics and status checks to check the state of your environment.
- Stop or reboot your EC2 instances.
- List CloudWatch alarms by state or time.
- View CloudWatch graphs.
- Examine the automated actions configured for each CloudWatch alarm.
- View detailed AWS service health status, including recent AWS service events and notifications.
Here’s a tour:
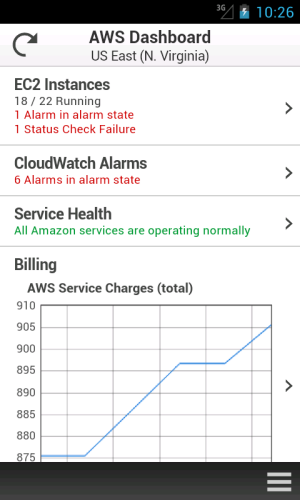
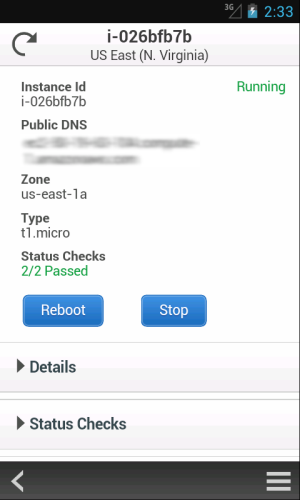
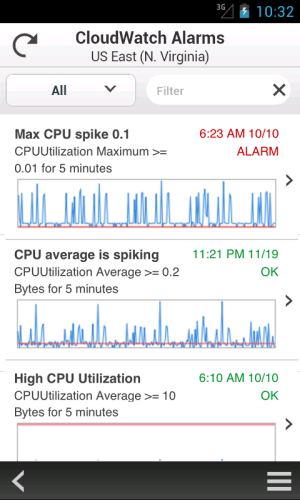
We plan to add support for additional services very quickly, so stay tuned (and use the app’s feedback function to tell us what you think). We are also planning to support mobile devices running other operating systems.
Download the AWS Management Console for Android and get started today.
By the way, the Management Console team is hiring! If youre interested in building web or mobile user interfaces, check out our open positions:
- Software Development Engineer, AWS Management Console
- Senior Mobile Developer, AWS Management Console
— Jeff;
Identity Federation to the AWS Management Console
In August, we announced that AWS Identity and Access Management (IAM) added support for Identity Federation. This enabled customers to use their existing identities (e.g. users) to securely access AWS APIs and resources using IAM’s fine-grained access controls, without the need to create an IAM user for each identity.
Today we are announcing that we have extended IAMs Identity Federation functionality to also enable federated users to access the AWS Management Console. This allows you to enable your employees to sign in once to your corporate directory, and then use the AWS Management Console without having to sign in to AWS, providing single sign-on access to AWS.
In my previous post on the topic of Identity Federation, I discussed how you could setup an identity broker, which calls our Security Token Service (STS), requesting temporary security credentials to provide your users access to AWS. You explicitly specify the permissions that these temporary credentials give your users, as well as control the amount of time (1 to 36 hours) these credentials are valid for. Well, these same temporary security credentials can now also be used to access the AWS Management Console.
Here’s the basic flow:
 |
User signs in to the enterprise network with their enterprise credentials. |

|
|
 |
User browses to an internal site and clicks on Sign in to AWS Management Console.
Page calls identity broker. Identity broker validates access rights and provides temporary security credentials which includes the user’s permissions to access AWS. The page includes these temporary security credentials as part of the sign-in request to AWS. |

|
|
 |
User is logged in to the AWS Management Console with the appropriate IAM policy. |
If you have already built an identity broker, perhaps using our sample application, to enable Identity Federation to AWS service APIs for users in your enterprise directory, youre already most of the way there. All you need to do is implement an internal web page with redirect links to the AWS Management Console, and include the temporary security credentials as part of the sign in request. Below is some simple Ruby code sample that shows how to do just that (just replace the highlighed items with your own identifiers and URLs):
-
require ‘rubygems’
-
require ‘json’
-
require ‘open-uri’
-
require ‘cgi’
-
require ‘aws-sdk’
-
-
# The temporary credentials will normally come from your identity
-
# broker, but for simplicity we create them in place
-
sts = AWS::STS. new ( :access_key_id => “*** Your AWS Access Key ID ***”,
-
:secret_access_key => “*** Your AWS Secret Access Key ***” )
-
-
# A sample policy for accessing SNS in the console.
-
policy = AWS::STS::Policy. new
-
policy. allow ( :actions => “sns:*”,:resources => :any )
-
-
session = sts. new_federated_session (
-
“UserName”,
-
:policy => policy,
-
:duration => 3600 )
-
-
-
# The issuer parameter specifies your internal sign-in
-
# page, for example https://mysignin.internal.mycompany.com/.
-
# The console parameter specifies the URL to the destination tab of the
-
# AWS Management Console. This example goes to the sns console.
-
# The signin parameter is the URL to send the request to.
-
issuer_url = “https://mysignin.internal.mycompany.com/”
-
console_url = “https://console.thinkwithwp.com/sns”
-
signin_url = “https://signin.thinkwithwp.com/federation”
-
-
# Create the signin token using temporary credentials,
-
# including the Access Key ID, Secret Access Key, and security token.
-
-
session_json = {
-
:sessionId => session. credentials [ :access_key_id ],
-
:sessionKey => session. credentials [ :secret_access_key ],
-
:sessionToken => session. credentials [ :session_token ]
-
}. to_json
-
-
get_signin_token_url = signin_url + “?Action=getSigninToken&SessionType=json&Session=” + CGI. escape (session_json )
-
returned_content = URI. parse (get_signin_token_url ). read
-
signin_token = JSON. parse (returned_content ) [ ‘SigninToken’ ]
-
signin_token_param = “&SigninToken=” + CGI. escape (signin_token )
-
-
# The issuer parameter is optional, but recommended. Use it to direct users
-
# to your sign-in page when their session expires.
-
issuer_param = “&Issuer=” + CGI. escape (issuer_url )
-
destination_param = “&Destination=” + CGI. escape (console_url )
-
-
login_url = signin_url + “?Action=login” + signin_token_param + issuer_param + destination_param
-
You can control the user name displayed in the upper right corner of the AWS Management Console when your user logs in. You can also optionally provide an “Issuer” URL when signing your users in. This URL will then be displayed to the user when their credentials expire, so they can re-authenticate with your identity system before continuing to use the AWS Console.
The following services support Identity Federation to the AWS Management Console today: Amazon EC2, Amazon S3, Amazon SNS, Amazon SQS, Amazon VPC, Amazon CloudFront, Amazon Route 53, Amazon CloudWatch, Amazon RDS, Amazon ElastiCache, Amazon SES, Elastic Load Balancing, and IAM. We’ll of course be adding support for additional service consoles over time (the busy Amazon DynamoDB team is already working on it!).
— Jeff;